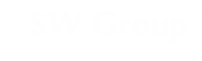Over the past 100 years, the automobile industry has been the driving force of economic growth. The automotive industry continues to lead the technological transformation, making cars a safe, comfortable and efficient way to transport. But so far, these are only little by little to increase and evolve, rather than revolutionary major changes. With the emergence of a self-driving car, we are also on the starting point of a revolutionary change. In order to lead this change without compromising safety performance, we need to carefully study the system-level risk from the design time to the IC level and its mitigation measures.
Automatically driving a car is really cool. After all, who does not want to speed up the speed of 150MPH, while watching "Harry Potter" (Harry Potter), without having to worry about driving it? But they are not just cool so simple. They can provide solutions for some of the most important and important issues - helping to reduce car accidents, save millions of hours of waste in traffic congestion, and wastage of urban space in car parks, which are only a small part of them Example only.
In order to make the dream of driving a car automatically, you need to combine several technologies to work with each other. Advanced Driving Assistance System (ADAS) enables better situational awareness and control to make driving simpler and more secure. ADAS technology can use the vehicle built-in system - that is, vehicle resident systems such as vision and camera systems, as well as sensor technology, or vehicle-to-vehicle (V2V) or vehicle-to-infrastructure (V2I) systems V2X), the use of intelligent, interconnection-based network.
The V2X communication uses the dedicated short-range wireless communication unit on the circuit board to transmit security-related information such as vehicle speed and body size, advance direction, brake status to other vehicles and receive the same information about other vehicles from these messages. V2X network using multi-hop (multi-hop) technology, through the other nodes to send this information, in order to achieve long-distance communication. Farther detection distances and the ability to observe corners or other vehicles help to alert the driver if the vehicle equipped with V2X is found earlier than the sensor, camera, or radar.
Automatic driving chart
With the maturity of these technologies, the most important factor to be able to successfully deploy is reliability and field performance. The history of automotive electronic systems has always been a problem, especially the most recent record. We have learned about the fragility of the electronic access control system and the events of the self-accelerating car. Two "moral" hackers have been able to control Jeep Grand Cherokee and get out of control with the media headlines by showing the vulnerability of remote access. These and other events all reveal the potential challenges that we need to overcome.
• V2V and V2I communication
• Use a mobile device, U disk or MP3 device
• Aftermarket and repair / diagnosis
The security challenge rises with each node connected to the outside world. There are several such nodes in the connected car, and if it is not connected to the Internet, it communicates with another vehicle that is part of the V2V network. In these vehicles, it must be ensured that communication with the outside world is taken from proven sources and is not tampered with during transmission.
In order to ensure security, the designer must proceed from the underlying hardware, usually need to solve the problem as follows:
• Hardware integrity - hardware prevention / detection tampering
• The completeness and authenticity of vehicle software and data - does not allow unauthorized changes to any vehicle software, or must be modified
• The integrity and authenticity of vehicle communication - the receiver must be able to detect unauthorized data changes
• Confidentiality of vehicle communications and data - confidential data that is not allowed to be transmitted or stored is unauthorized
• Prove the completeness and authenticity of the platform to other (remote) entities - the ability to demonstrate the integrity and authenticity of the platform configuration
• Access control of vehicle data and resources - for availability and well-defined access
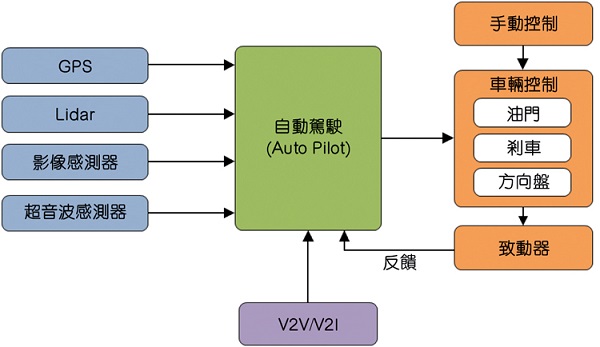
Challenges can be grouped into three main areas:
• Security hardware - the underlying hardware is very secure, must not be tampered with, and can form the source of trust;
• Design safety - The design built on the hardware is very safe and can not be tampered with;
• Data security - All data communication types are safe and reliable. 20170622_Microsemi_TA31P2 Figure 2: Multiple hierarchical approaches are critical to securing hardware, enhancing design security, and locking data security.
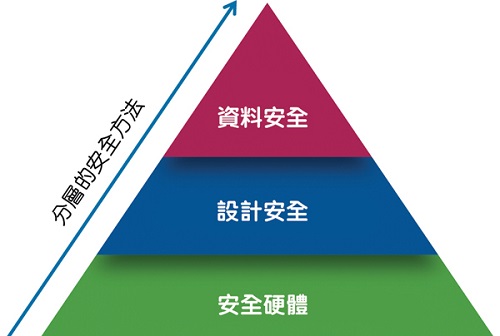
Multiple hierarchical approaches are critical to ensuring hardware, enhanced design security, and locking data security
Ensure that system security begins with securing hardware. Secure and trusted hardware forms the basis for a secure system. It provides the necessary building blocks that can be used to authenticate, authorize communication and action. This is true for any system, especially for V2X systems.
In order to achieve reliable V2V / V2I communication, it must be ensured that the communication is from a known source and is not changed during transmission. In order to prove authenticity, the sender of the information must provide the recipient with some form of identification that can be verified to confirm that the information is from the correct source. This can be achieved using symmetric or asymmetric encryption techniques.
For V2X networks, due to the complexity and scale of the network, symmetric encryption can not usually be used, but asymmetric encryption is used, and an extensible approach is provided to connect the number of nodes that the network may need. In order to achieve this, each node will use a private key, for each transmission of information signed digital signature. The receiving end verifies the digital signature with the public key transmitted to all the receiving nodes. This method is not only scalable than the symmetric encryption scheme is good, but also easier to replace the wrong node.
But this approach also brings another question: how to ensure that each node used by the key and public key is true and not tampered with?
The best possible solution to the first part of the problem is the use of a silicon IC's biometric signature, which is based on a small entity change in each component's production process. These process changes can never be the same, can not be copied, and no two ICs have the same process change, so Amotech provides a unique signature for each component. This signature is called the entity non-copy function (PUF). In addition to being copied, the key that uses PUF is usually implemented at the atomic level and is therefore difficult to capture by hackers. ICs can base PUF on several physical factors, such as memory components, logic latency, and resistance. The SRAM-based IC utilizes the unique random start state of the SRAM cell to generate the key, which is safer because the state of the cell is erased at power down.
The second part of the problem can be addressed through the Public Key Infrastructure (PKI). PKI is a system that creates, stores, and distributes digital certificates to validate a specific public key that belongs to an entity. PKI can create a digital certificate that maps the public key to an entity and securely stores the credentials in the central repository and, if necessary, can be removed.
In the PKI system, the certification authority (CA) uses its own key to sign a digital signature for its public key to authenticate all nodes. The most common public key authentication format is X.509. When a device uses its key to transmit information and digitally sign it, the information can be verified using the public key of the device. The device can also send its X.509 credentials to all nodes that receive its information so that they can have their public key. X.509 certificate, including the public key of the device, can also be CA's public key in the receiving end to verify; CA's public key will be placed in advance of all nodes, and is essentially trusted. With this scheme, since the signature used by the transmitter can be verified by the receiver, it is possible to establish a validated, credential-based hierarchical trust chain. This solution also ensures easy detection of manufactured equipment.
The size of the electrical and / or electronic content in today's vehicles has shifted the attention of the industry to ensure that the content does not pose any threat to the system or interface equipment and, if threatening, can take precautionary or corrective action.
In particular, as the industry moves towards the direction of intelligent vehicle control, human life is being handed over to sensors, microcontrollers (MCUs) and algorithms to control; at the same time, with the advent of electric vehicles, the size of electrical and / or electronic content Increase even more than ever. Therefore, the next step to the advanced driving support system must seriously consider the hidden system-level risks and the resulting security risks. From the design time has been extended to the IC level, the entire system must take security measures.